[ FREE ][ more than 15 gb for free ] Offcloud vs Bitport vs Seedr :which is best among three to direct download from torrent to cloud storages like google drive ,one drive ,dropbox etc.

Offcloud : [RECOMMENDED BY ME] [AS OF 17-july-2017]
Offcloud is a little different from the rest of the providers we’ve looked at, as it isn’t focused on downloading torrents. The company markets itself as “a simple, elegant and intuitive SaaS to retrieve any data from the cloud.” We were surprised at the amount of different sources Offcloud supports for downloading, and it even has a ticket box that allows users to suggest new sites to support.
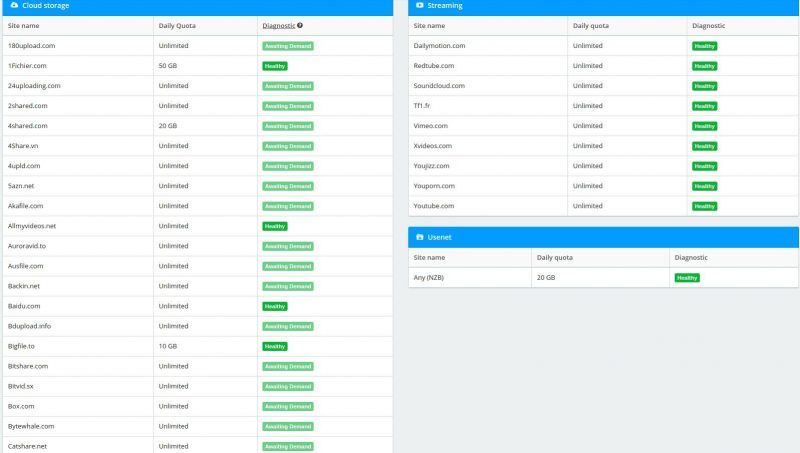
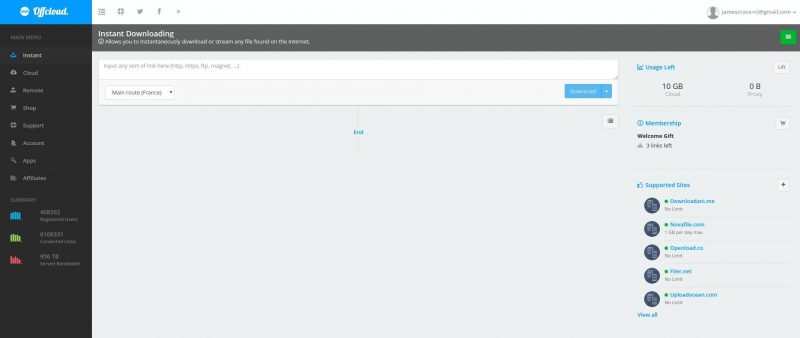
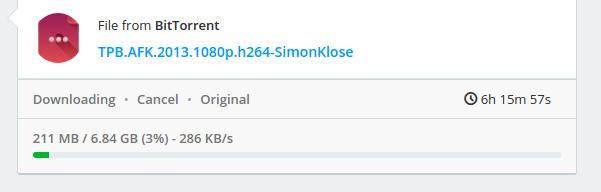
Note that Off-cloud doesn’t intend to act as a “seedbox,” which is a server used to boost a user’s ration on private trackers by perpetually seeding a torrent. A spokesperson for Offcloudstated that they typically only seed torrents on a 1:1 ratio, uploading the exact amount they downloaded. For users that rely on public trackers or don’t care about the ratio, Off-cloud is a fine solution.
If you’re only looking for a cloud torrent provider, Off-cloud may seem like overkill. But at $59.99 a year, it offers unlimited storage and bandwidth which makes for a better deal when you consider the limited storage offered by other providers. With all the feature included with Off-cloud, it’s easily one of the best options available.
| Price | Storage space | Number of torrents | |
|---|---|---|---|
Free
|
Free
|
10GB
|
3 per month
|
The Good Kit
|
$9.99 per month
|
Unlimited
|
Unlimited
|
The Useful Partner
|
$59.99 per year
|
Unlimited
|
Unlimited
|
Bitport.io
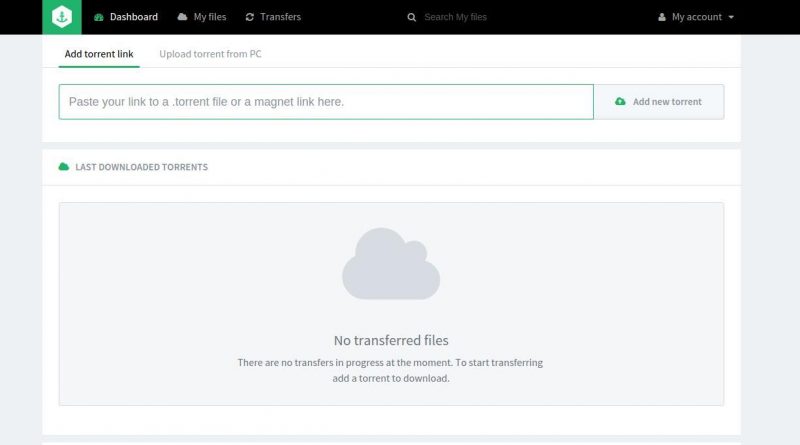
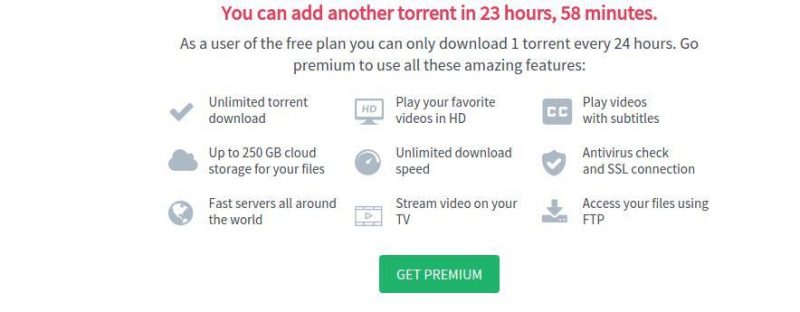
Bitport.io also seeds to a 1:1 ratio, but paid users can contact tech support and have this changed to a custom ratio. It’s a simple service, lacking extra features, but it serves its purpose well and at an affordable price.
| Price | Storage space | Number of torrents | |
|---|---|---|---|
Free
|
Free
|
1GB
|
1 per day
|
Small
|
$5 per month
|
30GB
|
5 slots
|
Standard
|
$10 per month
|
100GB
|
10 slots
|
Big
|
$15 per month
|
250GB
|
20 slots
|
Seedr
Seedr is another torrent service that offers a spartan interface and great usability on a computer or mobile device. The free tier limits you to 2GB of storage but places no limitations on the amount of files you can download, as I deleted and tried various torrents to get an idea of overall speeds.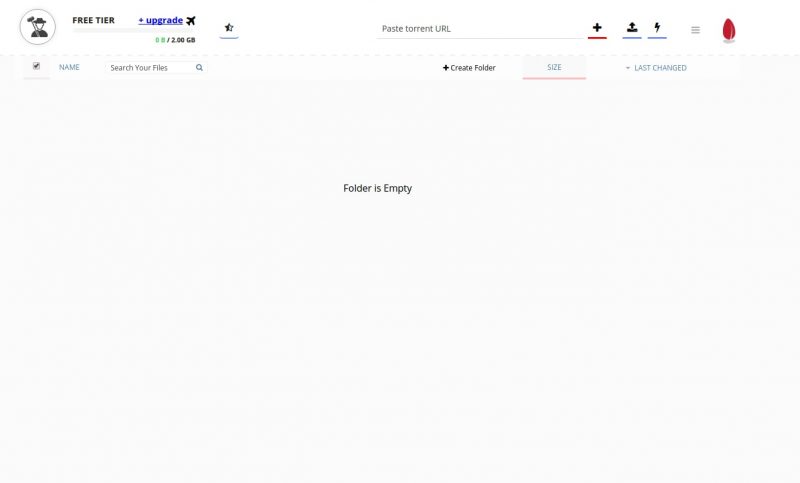


You download the .torrent to your device and simply upload it to Seedr, and they’ll seed it to either a 2:1 or 5:1 ratio depending on your plan. Seedr offers fast, often instant downloads of torrents, and let’s you stream your media right away on whatever devices you own. Paid tiers start at $6.95 a month for a simple, fast service to take your torrenting to the next level, in the cloud.
| Price | Storage | Number of torrents | |
|---|---|---|---|
Free
|
Free
|
2GB
|
N/A
|
Basic
|
$6.95 per month
|
30GB
|
2 slots
|
Pro
|
$9.95 per month
|
100GB
|
5 slots
|
Master
|
$19.95 per month
|
1TB
|
25 slots
|
Cloud Torrenting and Privacy

There is always the chance that the government could have a court compel a provider to hand over logs, and depending on the provider this could include your IP address and the list of files you have downloaded or stored under your account. The chances of this happening are unlikely, as services like Put.io have been active for years now without facing legal issues.
There are legitimate uses for torrenting, and the providers do not knowingly offer illegal content. They simply provide users with a way to quickly and securely access content on the web and store it. To date, there hasn’t been a single case of one of these providers handing over user data.
Comments
Post a Comment
share your thoughts ....